+
-
 +
+  -
-  +
+  -
- +
-
 +
+  -
-
AdGuard.com |
Wiki |
Reddit |
Twitter |
Telegram
-
+
- 

+
-


+
- 

+
- 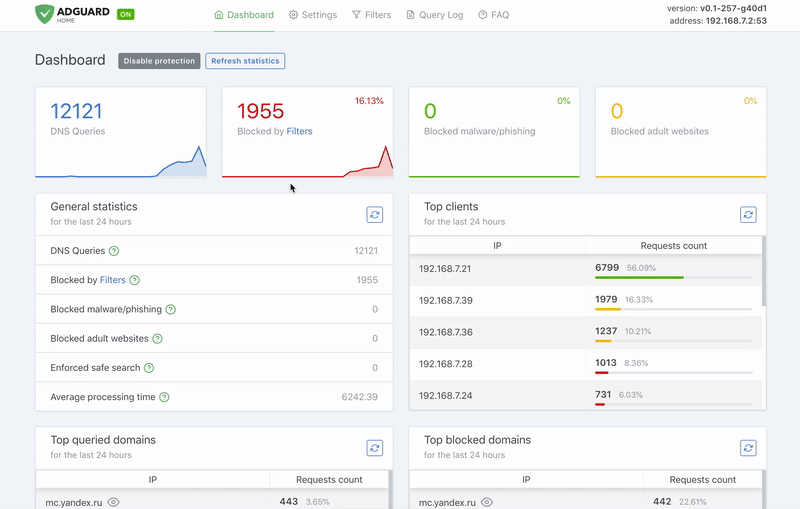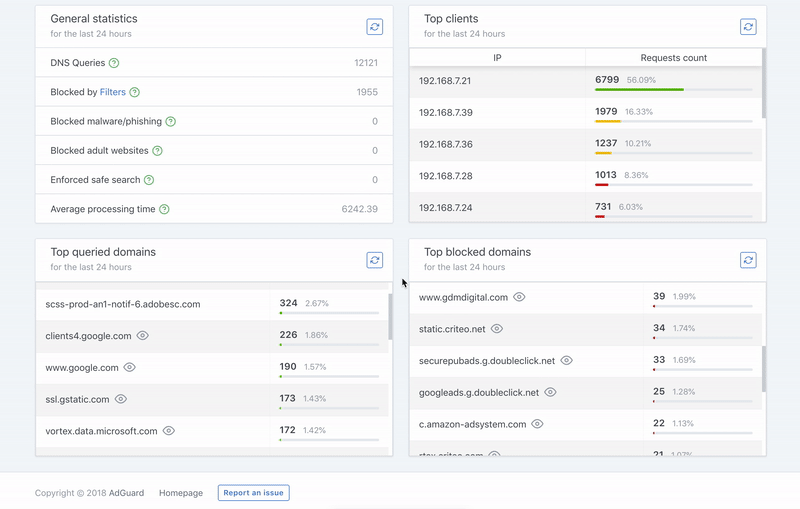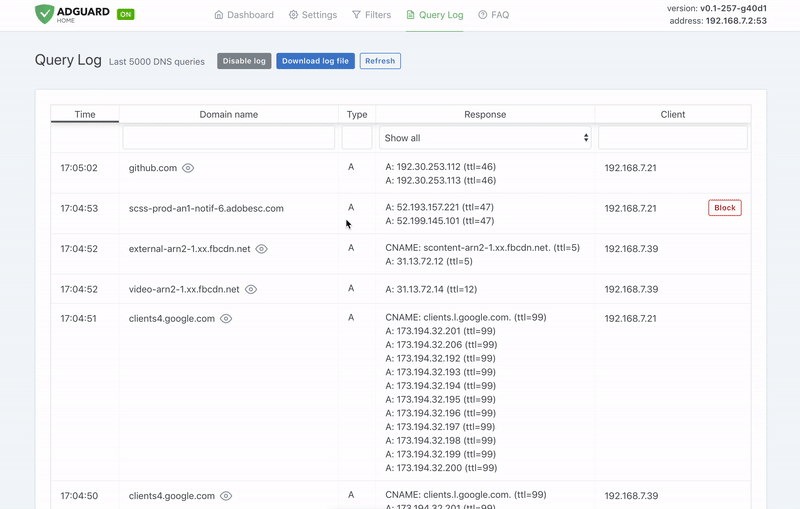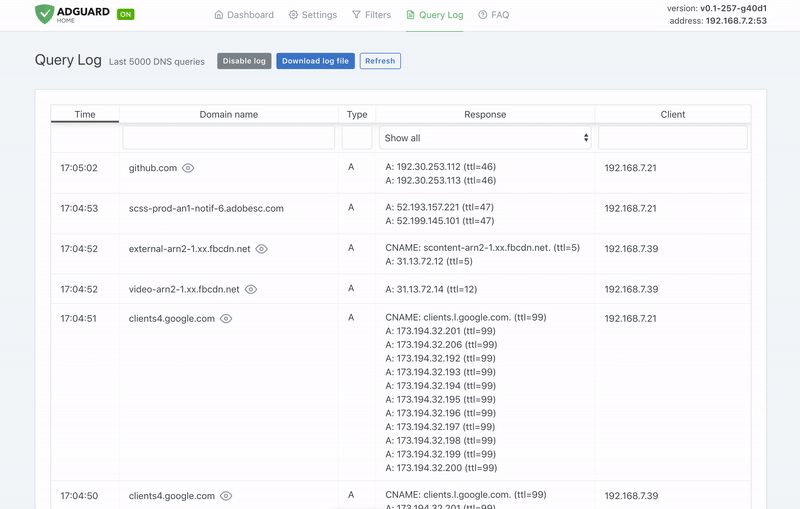 +
+ 
h3://unfiltered.adguard-dns.com/dns-query: quic://unfiltered.adguard-dns.com: